Hospital Cybersecurity Toolkit 2026: Practical Solutions for US IT

This essential toolkit for US hospital IT teams focuses on providing actionable, practical solutions for implementing cybersecurity best practices in hospitals by 2026, ensuring robust protection against escalating digital threats.
The landscape of healthcare technology is evolving at an unprecedented pace, bringing incredible advancements but also significant cybersecurity challenges. For US hospital IT teams, the task of safeguarding sensitive patient data and critical infrastructure from increasingly sophisticated cyber threats is more vital than ever. This comprehensive guide, a 2026 educational toolkit, is designed to equip you with the practical solutions needed for successfully implementing cybersecurity best practices in hospitals, ensuring resilience and maintaining patient trust in a rapidly changing digital world.
Understanding the evolving threat landscape in healthcare
The healthcare sector remains a prime target for cybercriminals, with breaches leading to severe financial, reputational, and operational consequences. Understanding the nature and evolution of these threats is the first step toward building a robust defense. We are not just talking about data theft; ransomware attacks can cripple hospital operations, directly impacting patient care and even lives.
As medical devices become more interconnected and telemedicine expands, the attack surface for bad actors grows exponentially. The sheer volume of sensitive personal health information (PHI) held by hospitals makes them particularly attractive. Cybercriminals are constantly innovating, developing new methods to exploit vulnerabilities, often outpacing traditional security measures.
The rise of sophisticated attacks
Modern cyber threats go beyond simple phishing. We now see highly organized, state-sponsored attacks and sophisticated ransomware-as-a-service models. These groups are well-funded and persistent, making it crucial for hospitals to adopt advanced, proactive security postures. They exploit human error, software vulnerabilities, and supply chain weaknesses.
- Ransomware: Attacks that encrypt critical systems and data, demanding payment for their release, often causing significant operational downtime.
- Phishing and Social Engineering: Deceptive tactics used to trick employees into revealing credentials or installing malware.
- Insider Threats: Malicious or negligent actions by current or former employees with access to hospital systems.
- IoT/IoMT Vulnerabilities: Exploitation of weaknesses in connected medical devices and other internet-of-things devices within the hospital network.
Regulatory pressures and compliance challenges
Maintaining compliance with regulations like HIPAA, HITECH, and emerging state-specific laws adds another layer of complexity. Non-compliance can result in hefty fines and legal repercussions. IT teams must continuously adapt security practices to meet these evolving legal requirements, ensuring all data handling processes are secure and auditable.
In conclusion, the dynamic nature of cyber threats coupled with stringent regulatory demands necessitates a constant, adaptable approach to cybersecurity in hospitals. Proactive threat intelligence and continuous staff training are no longer optional but essential components of a resilient security strategy.
Establishing a strong cybersecurity foundation: core principles
Building a resilient cybersecurity program starts with a solid foundation of core principles. This involves more than just installing antivirus software; it requires a holistic approach that integrates security into every aspect of hospital operations and culture. Without these fundamental elements, any advanced security measure will likely prove insufficient.
A strong foundation ensures that security is not an afterthought but a primary consideration from the initial design of systems to their daily operation. This proactive stance helps mitigate risks before they can fully materialize, reducing the impact of potential breaches. It emphasizes a structured and systematic approach to protection.
Implementing the NIST cybersecurity framework
The National Institute of Standards and Technology (NIST) Cybersecurity Framework offers a flexible, risk-based approach to managing cybersecurity activities and reducing cyber risk. For hospitals, adopting this framework provides a clear roadmap for improving security posture. It’s not a one-time implementation but an ongoing cycle of improvement.
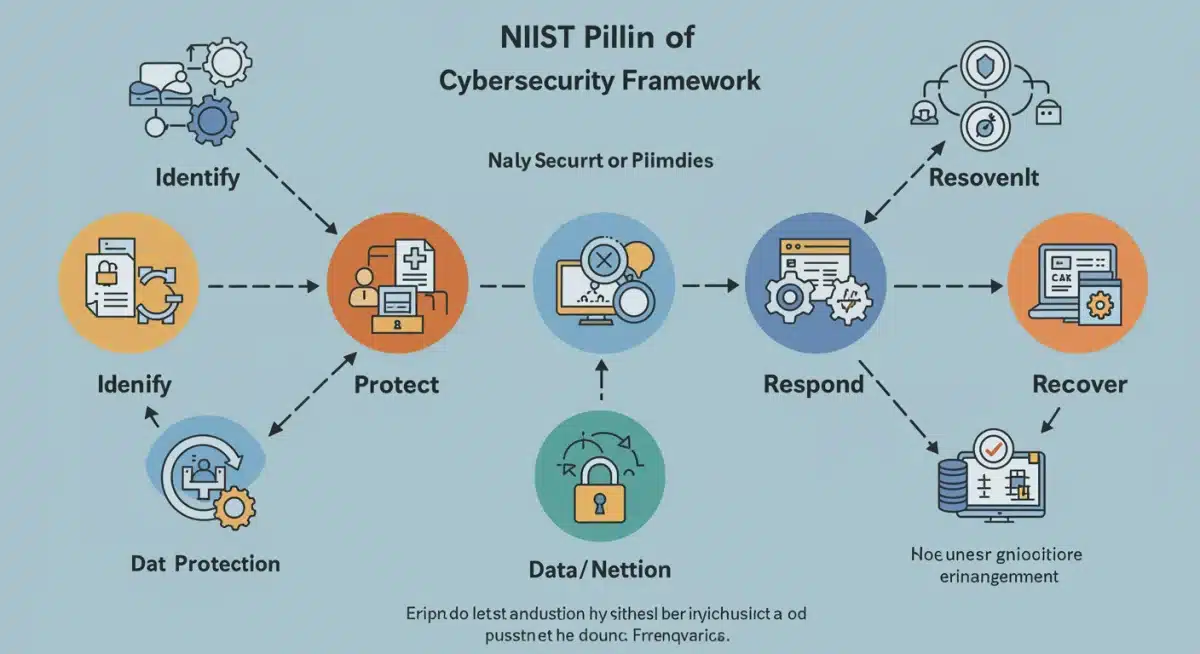

- Identify: Develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect: Develop and implement appropriate safeguards to ensure delivery of critical services.
- Detect: Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
- Respond: Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
- Recover: Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
Risk assessment and management
Regular and thorough risk assessments are crucial for identifying vulnerabilities and prioritizing security investments. Hospitals must understand where their most valuable assets lie, what threats they face, and how likely those threats are to materialize. This allows for targeted resource allocation and effective risk mitigation strategies.
Effective risk management is an ongoing process, not a static report. It involves continuous monitoring, reassessment, and adaptation to new threats and vulnerabilities. By consistently evaluating potential weaknesses, hospitals can stay one step ahead of cyber adversaries, building a dynamic defense.
In essence, establishing a strong cybersecurity foundation means adopting recognized frameworks, conducting diligent risk assessments, and fostering a culture where security is everyone’s responsibility. These bedrock principles are pivotal for enduring protection.
Strategic technological implementations for 2026
As we look towards 2026, technology continues to evolve, offering new tools and strategies to enhance cybersecurity. Strategic technological implementations are vital for hospitals to stay ahead of sophisticated threats. This involves not just adopting new software but integrating advanced systems that provide comprehensive, adaptive protection.
The focus must shift from reactive defense to proactive threat hunting and automated response. Leveraging cutting-edge technologies can significantly reduce human error, speed up detection times, and improve the overall efficiency of security operations. These implementations are critical investments for future security posture.
Advanced threat detection and response (MDR/XDR)
Managed Detection and Response (MDR) and Extended Detection and Response (XDR) solutions are becoming indispensable. These platforms offer continuous monitoring, threat intelligence, and automated response capabilities across various IT environments, including endpoints, networks, and cloud. They provide a more unified and intelligent approach to security than traditional tools.
- Unified Visibility: XDR platforms consolidate security data from multiple sources, offering a single pane of glass for threat detection.
- Automated Response: Capabilities to automatically isolate infected systems or block malicious traffic, minimizing damage.
- Threat Intelligence Integration: Utilizes global threat intelligence to identify emerging attack patterns quickly.
- Expert Analysis: MDR services provide access to security experts who can investigate and respond to incidents 24/7.
Zero trust architecture (ZTA) adoption
The principle of “never trust, always verify” underpins Zero Trust Architecture (ZTA). Instead of assuming that everything inside the network perimeter is safe, ZTA requires strict identity verification for every user and device attempting to access resources, regardless of their location. This significantly reduces the impact of compromised credentials or insider threats.
Implementing ZTA involves granular access controls, multi-factor authentication (MFA) for all access points, and continuous monitoring of user and device behavior. This architectural shift provides a much stronger defense against lateral movement within a network, a common tactic for attackers once they gain initial access.
In summary, strategic technological implementations like MDR/XDR and Zero Trust Architecture are foundational for 2026 cybersecurity in hospitals. They enable a more proactive, intelligent, and resilient defense against the ever-growing array of cyber threats.
Empowering the human element: training and awareness
While technology plays a crucial role, the human element remains the strongest link or the weakest in any cybersecurity chain. Even the most sophisticated systems can be bypassed by human error or successful social engineering. Therefore, empowering hospital staff through comprehensive training and continuous awareness programs is non-negotiable for effective cybersecurity.
A well-informed workforce acts as the first line of defense, capable of identifying and reporting suspicious activities before they escalate into major incidents. Investing in people means investing in a more secure environment, creating a culture where security is everyone’s shared responsibility, not just the IT department’s.
Comprehensive cybersecurity training programs
Training should not be a one-off event but an ongoing, evolving process tailored to different roles within the hospital. From front-line staff to executives, everyone needs to understand their role in maintaining security. This includes recognizing phishing attempts, understanding data handling protocols, and knowing how to report suspicious activities.
- Role-specific training: Tailoring content to the specific risks and responsibilities of different departments (e.g., clinical staff, administrative, IT).
- Phishing simulations: Regularly conducting simulated phishing campaigns to test staff awareness and provide immediate feedback and education.
- Data privacy education: Emphasizing the importance of patient data privacy and HIPAA compliance in daily workflows.
- Incident reporting procedures: Ensuring all staff know the clear steps to take when a potential security incident is identified.
Fostering a culture of security awareness
Beyond formal training, creating a pervasive culture of security awareness is vital. This involves regular communications, reminders, and making security an integral part of the organizational ethos. When employees understand the ‘why’ behind security policies, they are more likely to adhere to them and become proactive defenders.
Security awareness campaigns can utilize various formats, from posters and internal newsletters to short video modules and interactive workshops. The goal is to keep cybersecurity top-of-mind, making it a natural part of daily operations rather than an imposed burden. Leadership buy-in and active participation are key to fostering this culture.
Ultimately, the human firewall is as critical as any technical solution. By empowering staff through ongoing education and fostering a strong security culture, hospitals can significantly reduce their vulnerability to cyber threats, making them more resilient by 2026.
Securing medical devices and operational technology (OT)
The increasing connectivity of medical devices (IoMT) and operational technology (OT) in hospitals presents a unique and growing cybersecurity challenge. These devices, ranging from MRI machines to infusion pumps, are often legacy systems not designed with modern cybersecurity in mind, yet they are critical to patient care. Securing them is paramount.
Integrating these devices into the broader hospital network without adequate protection creates significant vulnerabilities that can be exploited by attackers. A breach involving a medical device could not only expose patient data but also directly impact the functionality of life-sustaining equipment, posing a direct threat to patient safety.
Inventory and risk assessment of all connected devices
The first step in securing IoMT and OT is to gain complete visibility. Hospitals need a comprehensive inventory of all connected devices, understanding their function, operating system, network dependencies, and potential vulnerabilities. Many devices might be unknown to IT, creating shadow IT risks.
- Device Discovery: Utilizing network scanning tools and asset management systems to identify every connected device.
- Vulnerability Assessment: Identifying known vulnerabilities associated with each device model and software version.
- Risk Prioritization: Assessing the potential impact of a compromise for each device on patient safety, data integrity, and operational continuity.
Segmentation and specialized security controls
Once devices are identified and assessed, network segmentation is a critical strategy. This involves isolating IoMT and OT devices from the main IT network, placing them in their own secure segments. This limits an attacker’s ability to move laterally from one compromised device to others or to the core hospital network.
Specialized security controls are also necessary for these devices. Traditional endpoint protection often isn’t compatible with or suitable for many medical devices. Solutions might include micro-segmentation, intrusion detection/prevention systems (IDPS) specifically for OT networks, and regular patching where feasible. For legacy devices that cannot be patched, strong compensating controls are essential.
Effectively securing medical devices and operational technology requires a dedicated strategy focused on discovery, assessment, segmentation, and the application of tailored security controls. This ensures that the advancements in connected care do not inadvertently become gateways for cyber threats.
Incident response and business continuity planning
Even with the most robust cybersecurity measures, incidents can and will occur. Therefore, having a well-defined and regularly tested incident response plan (IRP) and business continuity plan (BCP) is crucial for any hospital. These plans dictate how an organization will react to and recover from a cyberattack, minimizing disruption and damage.
The ability to respond quickly and effectively can determine the difference between a minor inconvenience and a catastrophic event. These plans are not just about technical recovery; they also encompass communication strategies, legal obligations, and maintaining patient care during disruption. Preparation is the key to resilience.
Developing and testing incident response plans
An incident response plan should clearly outline roles, responsibilities, communication protocols, and technical steps for detecting, analyzing, containing, eradicating, and recovering from cyber incidents. It should be a living document, regularly reviewed and updated to reflect new threats and organizational changes.
- Clear Roles and Responsibilities: Defining who does what during an incident, from initial detection to executive communication.
- Communication Strategy: Establishing internal and external communication channels, including notifications to regulators, patients, and media.
- Technical Playbooks: Step-by-step guides for technical teams to follow for common incident types (e.g., ransomware, data breach).
- Regular Drills and Tabletop Exercises: Conducting simulations to test the effectiveness of the plan and identify areas for improvement.
Business continuity and disaster recovery strategies
Beyond incident response, hospitals must have comprehensive business continuity plans to ensure essential patient care services can continue during and after a significant cyber event. This includes strategies for operating with limited IT systems, manual workarounds, and data backup and recovery procedures.
Disaster recovery focuses on restoring IT systems and data. This means having robust backup solutions, geographically dispersed data storage, and tested recovery procedures. The goal is to minimize downtime and ensure the swift return to normal operations, protecting patient welfare and financial stability.
In conclusion, thorough incident response and business continuity planning are indispensable components of a comprehensive cybersecurity strategy. Proactive planning and regular testing ensure that hospitals can effectively navigate and recover from inevitable cyber incidents, safeguarding both data and lives.
Future-proofing hospital cybersecurity: 2026 and beyond
As technology advances, so too do the methods of cybercriminals. Future-proofing hospital cybersecurity means adopting a forward-thinking approach, anticipating emerging threats, and investing in adaptive defenses. The year 2026 is not a finish line but a milestone in an ongoing journey of securing healthcare. This requires continuous innovation and vigilance.
Staying ahead means embracing new paradigms like artificial intelligence (AI) and machine learning (ML) for security, understanding the implications of quantum computing, and fostering strong collaborations across the healthcare ecosystem. A static security posture will inevitably fail against a dynamic adversary.
Leveraging AI and machine learning for security
AI and ML are revolutionizing cybersecurity by enabling faster and more accurate threat detection, anomaly identification, and automated response. These technologies can process vast amounts of data to identify subtle patterns indicative of sophisticated attacks that might evade human analysts or rule-based systems.
- Predictive Analytics: Using AI to forecast potential attack vectors and vulnerabilities based on historical data and threat intelligence.
- Behavioral Analytics: Identifying unusual user or device behavior that could signal a compromise.
- Automated Malware Analysis: Rapidly dissecting new malware strains to understand their capabilities and develop countermeasures.
- Orchestrated Response: AI-driven systems can orchestrate responses across multiple security tools, enhancing efficiency.
Inter-organizational collaboration and threat intelligence sharing
Cyber threats often transcend individual organizations. Hospitals can significantly enhance their defenses by participating in threat intelligence sharing initiatives and collaborating with other healthcare providers, government agencies, and cybersecurity firms. Sharing information about emerging threats and successful defense strategies benefits the entire sector.
Platforms like the Health Information Sharing and Analysis Center (H-ISAC) provide valuable resources for real-time threat intelligence and best practice sharing. Collective defense strengthens individual security postures. This collaborative approach creates a stronger, more informed front against common adversaries, benefiting all participants.
To future-proof cybersecurity, hospitals must embrace advanced technologies like AI and ML while actively engaging in collaborative threat intelligence sharing. These strategies will ensure adaptability and resilience against the evolving cyber landscape well beyond 2026, protecting patient care and data for years to come.
| Key Focus Area | Brief Description |
|---|---|
| Evolving Threats | Understanding sophisticated ransomware, phishing, and IoMT vulnerabilities in healthcare. |
| NIST Framework | Implementing a risk-based approach (Identify, Protect, Detect, Respond, Recover) for robust security. |
| Zero Trust | Adopting a “never trust, always verify” security model for all network access. |
| Staff Training | Empowering employees as the first line of defense through continuous education and awareness. |
Frequently asked questions about hospital cybersecurity
Hospitals hold vast amounts of sensitive patient health information (PHI), which is highly valuable on the black market. Additionally, the critical nature of patient care makes hospitals more likely to pay ransoms quickly, and their complex IT environments often present numerous vulnerabilities.
The NIST Cybersecurity Framework provides a structured, risk-based approach to managing and reducing cyber risks. It’s crucial for hospitals as it offers a flexible guide to improve their security posture, ensuring a comprehensive and adaptive defense against evolving threats.
Securing IoMT involves creating a comprehensive inventory of all devices, assessing their vulnerabilities, and implementing network segmentation to isolate them from the main IT network. Specialized security controls and regular patching, where possible, are also essential for protection.
Employee training is critical as human error is a leading cause of breaches. Comprehensive, ongoing training and awareness programs empower staff to recognize and report threats like phishing, making them the first line of defense and fostering a strong security culture.
Zero Trust Architecture (ZTA) operates on the principle of “never trust, always verify,” requiring strict authentication for all access attempts. Hospitals should adopt ZTA to minimize the impact of compromised credentials and prevent lateral movement within their networks, enhancing overall security.
Conclusion
The journey toward robust cybersecurity in US hospitals is a continuous and complex one, demanding vigilance, adaptability, and strategic investment. By focusing on understanding the evolving threat landscape, building a strong foundation with frameworks like NIST, implementing advanced technologies such as MDR/XDR and Zero Trust, empowering staff through comprehensive training, and diligently securing IoMT, hospitals can significantly enhance their defenses. Furthermore, proactive incident response planning and fostering inter-organizational collaboration will be pivotal in future-proofing healthcare against cyber adversaries beyond 2026. The ultimate goal remains clear: to protect patient data, ensure operational continuity, and maintain the trust that forms the bedrock of healthcare.





